Didn’t you know that there are around 2,200 cyberattacks per day, that could equate to more than 800,000 people being hacked per year. Cyberattacks occur for a wide range of reasons, and their motivations can be financial, political, ideological, or even simply malicious. As technology continues to advance, the prevalence and complexity of cyberattacks are expected to grow, highlighting the need for robust cybersecurity measures to mitigate the risks and consequences associated with them. To prevent such issues, it's crucial for testers to perform a penetration test. In our article, we'll share our own experiences and guide you on how to do it effectively.
Introduction to Penetration Test
Penetration testing, commonly referred to as "pen testing," involves a permissive intrusion into computer systems, web applications, or network devices. It essentially simulates a cyberattack, evaluating the security of these systems. The goal is to uncover weaknesses and access points to data and confidential information. This testing method can assess the strengths and vulnerabilities of individual computer systems or an entire network of devices within an organization.
Pen testers use the same tools and techniques employed by real attackers to gain unauthorized access to systems and data. It's a crucial component of an organization's security strategy, as it helps identify vulnerabilities that need attention before malicious actors exploit them. Additionally, pen testing measures the effectiveness of an organization's security controls and highlights areas where improvements are necessary
History of the Penetration Test
James P. Anderson, a pioneer in penetration testing, made significant contributions in the 1970s when computer security was in its infancy. He developed a structured approach for testing system security, a model still used today.
His innovations, beginning with a patent for one of the first multiprocessor systems in 1959, continued with the creation of the reference monitor in 1972, audit trail-based intrusion detection in 1980, and receiving the National Computer Systems Security Award in 1990.
Anderson introduced a structured approach to test system security, identifying vulnerabilities and planning authorized attacks to exploit weaknesses. This approach remains a foundational framework for penetration testing.
By the 1980s, the Computer Fraud and Abuse Act was enacted in response to concerns about computer communication security. In the 1990s, the "SANTA" tool was developed for network analysis, discovering vulnerabilities and forecasting potential threats.
In the 2000s, early developers embraced Agile methodologies, focusing on speed and automation. Traditional pentesting struggled to keep up with technological advancements. The demand for agile and rapid pentesting grew as more companies adopted the DevOps model. This shift led to the emergence of Pentest as a Service (PtaaS), especially relevant in 2020 with the rise of remote workforces and digital solutions, offering a modern approach to penetration testing.

What is a penetration test?
Penetration testing effectively simulates the tactics of potential attackers seeking to compromise a system or organization. The goal of penetration testing is not limited to checking off compliance requirements; it delves deeper into testing an organization's cybersecurity capabilities, people, and processes against real-world threats. By mimicking specific adversary tactics, techniques, and procedures (TTPs), penetration testers provide a realistic assessment of how a breach could occur, offering invaluable insights to enhance security measures.
Once the penetration testing phase concludes, the pen tester consolidates the findings into a comprehensive report. This report encompasses details on the identified vulnerabilities, their exploitation, data access, and the duration the tester remained undetected. The penetration testing report serves as a valuable resource for addressing network weaknesses and enhancing server security.
Penetration Testing Process
While the specific methodology may vary depending on the testing team and the target system, the general penetration testing process typically follows these five stages:
1. Planning and Reconnaissance
The first step involves gathering intelligence about the target system to understand its functionality, potential vulnerabilities, and security measures in place. This information is gathered through various reconnaissance techniques, such as open-source intelligence (OSINT), social engineering, and network scanning.
2. Scanning and Analysis
Once the reconnaissance phase is complete, the testing team uses various tools and techniques to scan the target system for open ports, vulnerabilities, and potential weaknesses. This may involve static analysis, which examines the system's code or configuration, or dynamic analysis, which observes the system's behavior in real-time.
3. Vulnerability Exploitation
Leveraging the information gathered in the previous stages, the testing team attempts to exploit identified vulnerabilities to gain unauthorized access to the target system. This may involve using techniques such as SQL injection, cross-site scripting, or buffer overflows.
4. Post-Exploitation and Privilege Escalation
If the testing team successfully gains access to the target system, they move into the post-exploitation phase. This involves maintaining access, exploring the system further, and attempting to escalate privileges to gain higher levels of access.
5. Reporting and Remediation
The final stage involves documenting the penetration testing findings in a comprehensive report. The report should outline the vulnerabilities discovered, the exploits used, the impact of the attack, and recommendations for remediation. The organization can then use this information to address security weaknesses and improve their overall cybersecurity posture.
Regular penetration testing provides organizations with a multitude of benefits, including proactive identification of security vulnerabilities, enhanced overall security posture, compliance with cybersecurity regulations, and peace of mind derived from regularly tested and fortified systems.
Rules in Penetration Testing
Rules of Engagement (RoE) is a document that deals with the manner in which the penetration test is to be conducted. The most common method is defining the scope of the test. The main methods are black-box, white-box, gray-box. Let's analyze them.
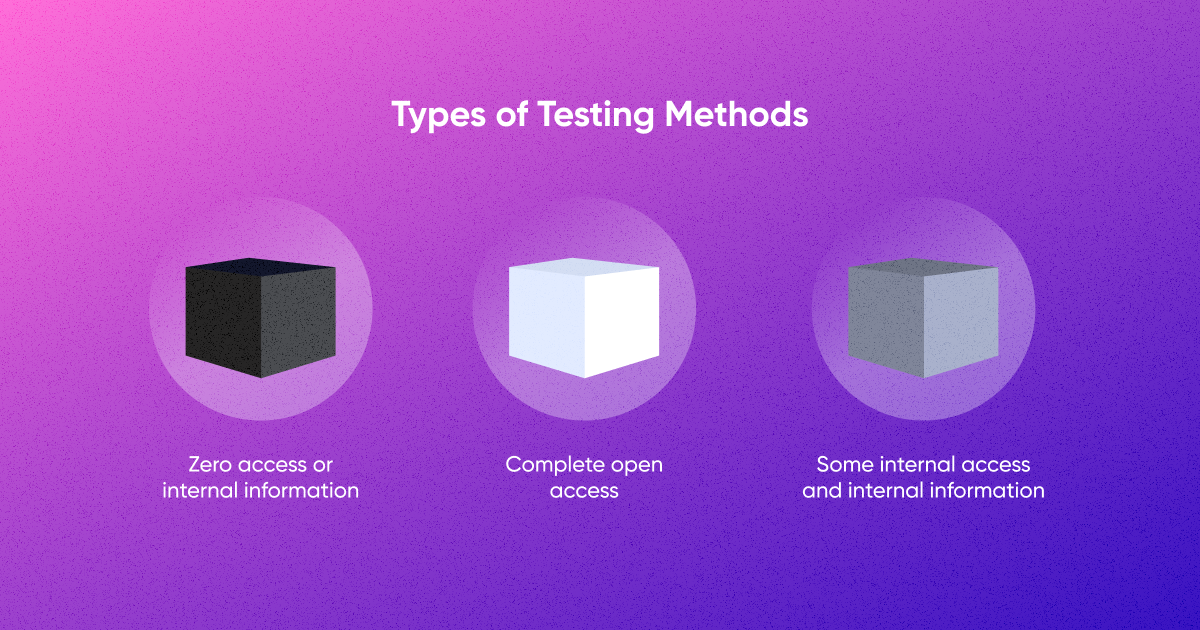
Black-box testing
The tester has no prior knowledge of the internal workings of the system being tested. They approach it as an external attacker would, with no access to the source code, architecture diagrams, or any other insider information. For example, black-box testing is widely used to identify vulnerabilities such as injection attacks, cross-site scripting (XSS), and other web-based threats. Or when an independent third party is tasked with assessing the security of a system, black-box testing is often chosen.
Mostly used in:
- External security assessment
- Third-party security audits
- User Interface (UI) and experience security
White-box testing
Testers have full knowledge of the internal workings of the system, including source code, architecture, and design. This approach allows testers to conduct a thorough examination of the system's internal structures. For example, when dealing with custom applications developed in-house, white-box testing becomes crucial.
Mostly used in:
- Compliance with coding standards
- Internal system evaluation
- Code-level vulnerability identification
Gray-box Testing
Testers have partial knowledge of the system—enough to guide their testing efforts effectively, but not a complete understanding. It adds a layer of realism by simulating the partial knowledge an attacker might gain through reconnaissance. For example, for systems that incorporate both off-the-shelf and custom components.
Mostly used in:
- Optimal resource utilization
- Simulating partial insider knowledge
- Balanced perspective
In addition, there are several more important rules in penetration test requirements.
Do not damage or disrupt production systems
The goal of QA specialist is to simulate real-world scenarios without causing harm. This may include steering clear of actions that could lead to data loss, availability issues, or performance degradation.
Unauthorized access is a strict no-go
Penetration testers should resist the temptation to use social engineering, brute force attacks, or any other methods that could compromise the security of systems and data.
Reporting is key
This involves providing a detailed account of the vulnerability, steps to reproduce it, and the potential impact it could have on the system. Clear and comprehensive reporting helps organizations understand the risks and take appropriate actions for remediation.
Post-testing cleanup
Post-testing cleanup is often overlooked but is crucial for maintaining the integrity of the systems. Removing any tools, backdoors, or implants used during the test ensures that the system returns to its original state and reduces the risk of lingering security issues.
Confidentiality
Test results should only be shared with authorized individuals. This means refraining from disclosing results on public forums or sharing them with unauthorized parties. Such discretion prevents the spread of sensitive information and maintains the security posture of the organization.
Penetration Testing Methodologies
There are various standards and methodologies that ensure the penetration test is authentic and covers all important aspects. Penetration testing methodologies play a crucial role by establishing a clear and structured path to follow throughout the testing process, enhancing both efficiency and effectiveness. Below, I list some of the most popular standards.
OSSTMM
OSSTMM (Open Source Security Testing Methodology Manual) ****is a comprehensive and open framework for penetration testing and security assessment. It focuses on the operational aspects of security testing and aims to provide a holistic understanding of security risks.
- Categorizes tests into three main sections: Information Security, Process Security, and Internet Security.
- Emphasizes metrics and measurement to assess the effectiveness of security controls.
- Provides a structured approach for assessing security from a human-centric perspective.
OWASP
Open Web Application Security Project is renowned for its focus on web application security. The OWASP Testing Guide and OWASP Application Security Verification Standard (ASVS) offer guidance on conducting penetration tests for web applications.
- Prioritizes web application security issues, including the OWASP Top Ten list.
- Encourages a proactive approach to integrate security into the entire software development lifecycle.
- Offers a wealth of resources, tools, and documentation for security professionals.
NIST
National Institute of Standards and Technology provides guidelines and standards for various aspects of cybersecurity, including penetration testing. The NIST Special Publication 800-115 focuses on information security testing and assessment.
- Aligns with the Risk Management Framework (RMF) to integrate penetration testing into the risk management process.
- Emphasizes a continuous and systematic approach to security assessment.
- Provides a structured framework for documenting and reporting findings.
PTES
Penetration Testing Execution Standard is a framework that provides a consistent and comprehensive guide for conducting penetration tests. It covers the entire penetration testing process, from initial planning to the final reporting phase.
- Divides the penetration testing process into seven stages: Pre-engagement, Intelligence Gathering, Threat Modeling, Vulnerability Analysis, Exploitation, Post Exploitation, and Reporting.
- Aims to standardize and improve the quality of penetration testing services.
- Emphasizes the importance of thorough documentation at each stage.
ISSAF
Information Systems Security Assessment Framework is designed to guide security professionals through the process of assessing the security of information systems. It provides a systematic approach to identifying and addressing security risks.
- Focuses on both technical and non-technical aspects of information security.
- Provides guidance on the entire assessment lifecycle, from scoping to reporting.
- Aims to enhance the efficiency and effectiveness of security assessments.
Each methodology has its strengths, and the choice of which to use may depend on factors such as the specific focus of the test, the type of systems being assessed, and organizational preferences. Combining elements from multiple methodologies is also a common practice to ensure a well-rounded and thorough penetration testing approach.
Types of the Penetration Test
Organizations can choose the type of penetration testing that is most appropriate for their needs. It is important to note that no single type of penetration testing can identify all vulnerabilities. Therefore, it is often recommended to combine multiple types of penetration testing to get a more comprehensive assessment of an organization's security posture.
Internal Penetration Test
Geared towards evaluating the security of internal networks, systems, and applications from within the organization itself. The emphasis lies in identifying vulnerabilities that could be exploited by insiders or attackers who have gained internal access. Emulate the actions of a determined insider by exploring the internal network with a focus on lateral movement and privilege escalation. This helps identify and address potential threats from within the organization.
External Penetration Test
This type aims to assess the security of outward-facing systems, including websites, servers, and network infrastructure. The primary focus is on pinpointing vulnerabilities that external attackers could exploit to gain unauthorized access. Simulate realistic external threats by considering the techniques and tactics commonly employed by external attackers. This ensures a more accurate representation of potential risks.
Web Application Penetration Test
Specifically targeting web applications, this type aims to uncover and exploit vulnerabilities in their design, implementation, or configuration. Common issues addressed include SQL injection, cross-site scripting (XSS), and insecure authentication mechanisms.Regularly update testing methodologies to align with evolving web application technologies and attack vectors. This ensures that the assessment remains relevant and effective against the latest threats.
Mobile Application Penetration Test
This assessment concentrates on evaluating the security of mobile applications across various platforms, such as iOS and Android. The goal is to identify vulnerabilities related to insecure data storage, communication, and unintended data leakage. Consider platform-specific security nuances for iOS and Android during testing.
Wireless Network Penetration Test
Focused on assessing the security of wireless networks, including Wi-Fi, to identify vulnerabilities and potential unauthorized access points. This type examines encryption protocols, authentication mechanisms, and overall wireless network security. Prioritize the assessment of Wi-Fi security protocols and configurations to identify vulnerabilities that could lead to unauthorized access. Pay attention to encryption strength and authentication mechanisms.
Physical Penetration Test
This type assesses the effectiveness of physical security measures, including access controls, surveillance, and security personnel. The primary goal is to identify weaknesses that could allow unauthorized individuals physical access to sensitive areas. Conduct a thorough reconnaissance phase to gather information about physical security measures and potential entry points.
Social Engineering Test
This evaluation targets the human element of security by simulating attacks that manipulate individuals into divulging sensitive information. It assesses the effectiveness of security awareness training and the organization's resilience against social engineering tactics. Customize social engineering scenarios based on the organization's industry and culture. This approach increases the relevance and effectiveness of the test in identifying human-related vulnerabilities.
Red Team vs. Blue Team Exercises
Simulating real-world attack scenarios (Red Team) and assessing the organization's defense and response capabilities (Blue Team). Regular debriefings enhance the learning experience and contribute to a more effective security posture.
Purple Team Exercise
This exercise combines elements of both Red Team and Blue Team approaches, fostering collaboration between offensive and defensive teams. The primary focus is on enhancing communication and coordination, leading to a more proactive and adaptive security strategy. Regular knowledge sharing enhances the overall security awareness of both teams, contributing to a more robust security strategy.
Best Penetration Testing Tools
Burp Suite
Burp Suite is a premier web application security testing tool widely adopted by security professionals for its robust features and effectiveness in identifying vulnerabilities.
Features
- Proxy: Facilitates interception and modification of HTTP/HTTPS requests.
- Scanner: Automated tool for identifying common web application vulnerabilities.
- Spider: Automates the mapping of web application structures for comprehensive assessments.
- Repeater: Allows repetition and modification of requests for vulnerability testing.
- Intruder: Automates attacks by varying parameters, aiding in vulnerability identification.
- Decoder: Assists in decoding and encoding data to analyze input processing.
- Collaborator: Identifies out-of-band vulnerabilities through a unique interaction domain.
- Extensibility: Supports extensions for customization and adaptability to specific testing needs.
Pricing
BurpSuite has 5 pricing editions, from $0 to $49,999. Additionally, users can take advantage of a free trial period.
Reviews
4.6/5 according to Gather.
Nmap
Nmap, short for "Network Mapper," is a renowned open-source network scanning tool. It is widely recognized for its versatility in network exploration and security auditing, making it an indispensable asset for network administrators, security professionals, and ethical hackers.
Features
- Host Discovery: Nmap excels in discovering devices on a network, providing a comprehensive view of active hosts.
- Port Scanning: It enables thorough port scanning to identify open ports and services running on target machines.
- Version Detection: Nmap can detect the version of services running on open ports, aiding in vulnerability assessment.
- Scriptable Interaction: Nmap offers scripting capabilities for customizing and automating tasks, enhancing flexibility.
- OS Fingerprinting: It can identify the operating system of a target host based on subtle network characteristics.
- Aggressive Scan Options: Nmap provides aggressive scan options for a more comprehensive and thorough assessment.
- Scripting Engine: The Nmap Scripting Engine (NSE) allows users to create and share custom scripts for specific tasks and detections.
- Output Formats: Nmap supports various output formats, making it adaptable to different reporting and analysis needs.
Pricing
Nmap has 12 pricing edition(s), from $7,980 to $98,980. No free trial.
Reviews
8.3/ 10 according to TrustRadius.
Metasploit
Metasploit is a leading penetration testing framework that stands out for its versatility and effectiveness in simulating real-world cyber attacks. Developed by Rapid7, it is widely adopted by security professionals, penetration testers, and ethical hackers to assess and enhance the security posture of systems.
Features
- Exploit Development: Metasploit's robust framework allows users to develop, test, and execute custom exploits, providing a comprehensive toolkit for identifying and addressing vulnerabilities.
- Payload Generator: It offers a variety of payload options for delivering exploits, including shellcode and other malicious payloads, facilitating thorough penetration testing.
- Post-Exploitation Modules: Metasploit includes a vast array of post-exploitation modules for actions like privilege escalation, lateral movement, and data exfiltration, enabling in-depth security assessments.
- Automated Exploitation: The framework provides automated exploitation capabilities, streamlining the process of identifying and exploiting vulnerabilities across diverse environments.
- Integration with Other Tools: Metasploit seamlessly integrates with other security tools and frameworks, enhancing its versatility and making it a valuable asset in complex cybersecurity ecosystems.
- Community and Collaboration: With an active and engaged user community, Metasploit encourages collaboration and knowledge-sharing, fostering a dynamic environment for staying updated on the latest threat vectors and exploits.
- Regular Updates: Rapid7 consistently updates Metasploit to address emerging security challenges and incorporate new features, ensuring it remains at the forefront of penetration testing tools.
Pricing
The current price for Metasploit Pro is around $15,000 per year. Also, you can visit https://www.rapid7.com/products/metasploit/download/pro/ to request a free trial license for Metasploit Pro. It can take up to 15 minutes to receive the email with your license key.
Reviews
9.3 out/10 according to TrustRadius.
sqlmap
SQLMap is a powerful open-source penetration testing tool specifically designed for detecting and exploiting SQL injection vulnerabilities. Positioned as a specialized tool, it caters to security professionals, ethical hackers, and penetration testers who focus on identifying and addressing SQL injection vulnerabilities in web applications and databases.
Features
- Automatic SQL Injection Detection: SQLMap excels in automating the detection of SQL injection vulnerabilities in web applications, saving time and providing accurate results.
- Support for Multiple Database Systems: SQLMap supports a wide array of database management systems, including MySQL, PostgreSQL, Oracle, and Microsoft SQL Server, ensuring versatility in its application.
- Detection of Blind SQL Injection: It is equipped to identify blind SQL injection vulnerabilities, where traditional methods might not directly reveal the results of the injected queries.
- Interactive Mode: SQLMap provides an interactive mode, allowing users to fine-tune and customize the exploitation process based on specific testing requirements.
- Options for Evading Detection: The tool includes evasion techniques to bypass security mechanisms and avoid detection during the testing process.
Pricing
Free of cost.
Reviews
4.3/ 5 according to g2.
Conclusion
If you are currently seeking a skilled QA tester for your project, explore our workflow here. Our experienced team, with an average of 5 years of experience per member, is ready to assist you in ensuring the security and reliability of your software. Feel free to contact us at any time to discuss your project requirements and explore how our QA testing services can contribute to the success of your endeavors.




