Didn’t you know that there are around 2,200 cyberattacks per day, which could equate to more than 800,000 people being hacked per year? Cyberattacks occur for a wide range of reasons, and their motivations can be financial, political, ideological, or even simply malicious. As technology continues to advance, the prevalence and complexity of cyberattacks are expected to grow, highlighting the need for robust cybersecurity measures to mitigate the risks and consequences associated with them. To avoid problems, make sure to create and follow a cybersecurity plan with your software development team. In this article, I'll be sharing the best practices for implementing a cybersecurity strategy, practices that our team follows and implements for our clients as well.
What is a Cybersecurity Strategy?
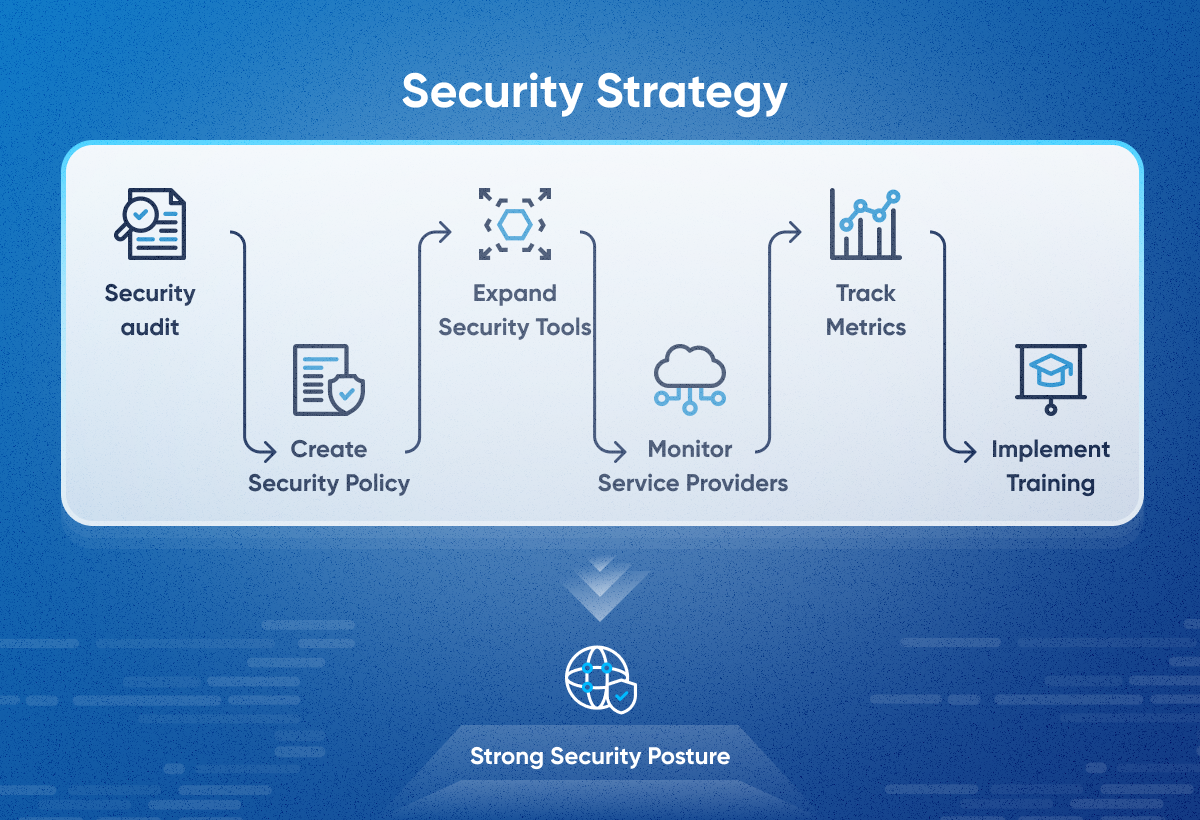
A cybersecurity strategy is a specific plan outlining how an organization will protect its digital assets and sensitive data from hacking and unauthorized access. It defines the organization's goals for cybersecurity, the threats it faces, and the controls it will put in place to mitigate those threats. An effective cybersecurity strategy is essential for any organization that wants to protect its data, systems, and reputation from cyberattacks. The general steps involved in creating a cybersecurity strategy include conducting a security audit, establishing security policies, monitoring service providers, implementing training, tracking metrics, and maintaining and updating the strategy.
Implementing Strong Access Controls
On this note, I would like to highlight the case of the well-known telecom company Kyivstar, boasting more than 20 million users. The digital infrastructure of Kyivstar suffered critical damage, leaving all subscribers without communication. This underscores the importance of consistently implementing this point.
Access to sensitive data, particularly customer data, is a pivotal aspect of cybersecurity. Regular access checks, role-based access, and the application of robust authentication methods, such as Multi-Factor Authentication (MFA), are crucial. MFA enhances security by requiring users to provide two or more verification factors to access a resource, significantly reducing the risk of unauthorized access.
Software Audits and Updates
Open-source software is often a primary target for cybercriminals. Companies in the finance sector must adhere to stringent data protection standards. Therefore, it is crucial to regularly audit and update licenses, software, and testing procedures. Our quality assurance team, for instance, can assist you with these measures.
At Movadex, we always recommend to our clients how crucial it is to test their website or app. Depending on your budget and our expert advice, we'll advise the type of testing your application needs, considering all the conditions mentioned earlier. This way, you can see examples of both manual testing and automated testing in action.
Compliance
Compliance, in the context of cybersecurity, refers to adhering to a set of established standards and regulations designed to protect sensitive information and systems from cyberattacks. For example, HIPAA in the healthcare industry, PCI DSS for payment card data, and GDPR for data privacy in the EU are some examples. But if talk about internal policies, there is an own set of security policies and procedures that employees must follow.
Why is compliance crucial in cybersecurity? Not following rules can mean big fines and legal trouble. Also, sticking to cybersecurity rules often makes incident response and risk management better, making operations smoother and saving costs.
Data Protection
Data breaches can seriously harm organizations, affecting finances, reputation, and legal standing. Encryption is a key tool for safeguarding data by converting it into a coded format that's unreadable without the right key, making it secure even if it's accessed by unauthorized parties.
A straightforward example is restricting access to sensitive data to authorized individuals and systems, accomplished through user authentication, authorization, and role-based access control.
Detection and Prevention
For instance, there are intrusion detection/prevention systems (IDS/IPS) that keep an eye on network traffic, looking for patterns and signs of compromise (IOCs) that could indicate an ongoing attack. When it comes to prevention, a crucial rule is setting up robust authentication and authorization measures, limiting access to sensitive data and systems to authorized users only. Additionally, remember to segment your network by dividing it into smaller sections, which can stop attackers from moving around and accessing critical systems, even if they breach the initial perimeter.
Cyber Training
The most valuable resource is people. That's why our specialists, including not just developers but everyone, regularly undergo cybersecurity courses. To boost your employees' cybersecurity knowledge, consider platforms such as Cybrary, Future Learn, and Code Academy.
What Security Risks Are Most Common?
Worldwide, 72.7% of organizations experienced a ransomware attack in 2023, as reported by Statista. Projections indicate that ransomware costs are expected to rise to approximately $265 billion USD annually by 2031, marking a significant increase from the $20 billion recorded in 2021, according to Cybersecurity Ventures.
Unsafe Password
According to various studies and reports, weak and default passwords are among the top causes of data breaches and cyber-attacks. The Verizon 2021 Data Breach Investigations Report found that 61% of breaches involved credential data.
Sadly, lots of companies have a big problem with using default or weak passwords like '123456' or 'password'. If users use these kinds of passwords for different accounts, it's like leaving the front door wide open for hackers to get important business info.
To enhance security beyond passwords alone, the implementation of Two-Factor Authentication (2FA) becomes crucial. 2FA involves providing users with two different forms of authentication to access their accounts.
Poor Code
Insecure code might skip crucial steps like checking inputs, encoding outputs, managing errors, and securing sensitive data properly. Additionally, inefficient code can hog resources, slowing down systems and opening doors for denial-of-service attacks. All of this creates opportunities for attackers. That's why it's essential to depend on developers who grasp cybersecurity principles. Lastly, testing is key. For instance, I penned an article about penetration testing, a method we apply to test our customers' products.
Legacy Software
Legacy software refers to outdated software still in use by some organizations, even though it's no longer supported by the vendor. This poses challenges for maintenance and security.
Since legacy software was designed in a different era, it often lacks the modern security protocols needed to counter today's advanced cyber threats. Integrating it with newer systems can be tricky, leading to compatibility issues that introduce additional security risks. It's like trying to fit a square peg in a round hole, creating weak points in the overall structure.
Lack of Maintenance
Poor maintenance can have severe consequences, including data breaches, financial losses, operational disruptions, and damage to reputation. That's why it's crucial to keep software and systems up-to-date with the latest security fixes. Over time, systems can become misconfigured, introducing hidden security risks. Regular monitoring and configuration checks are essential to ensure everything stays secure.
Denial-of-Service (DoS) Attacks
DoS attacks operate through various mechanisms, all aiming for one result: overwhelming the target system's resources. This downtime translates to lost revenue, disrupted operations, and costly mitigation efforts. Additionally, DoS attacks can create opportunities for attackers to exploit vulnerabilities and steal sensitive information.
Ransomware
Ransomware is a type of malware designed to exploit your valuable data. It functions by encrypting your files, rendering them inaccessible and effectively holding them hostage. Subsequently, attackers demand a ransom payment, typically in cryptocurrency, in exchange for the decryption key.
From ransom payments to operational disruptions, the financial impact of ransomware can be severe. One notable ransomware incident is the WannaCry attack in 2017. This attack affected hundreds of thousands of computers globally, exploiting a Windows vulnerability. The malware encrypted files on infected systems, prompting ransom payments in Bitcoin for decryption keys.
Zero-Day Attacks
These are newly discovered vulnerabilities that haven't yet been patched, making them particularly dangerous. These attacks target vulnerabilities in software or hardware that are unknown to the vendor or developers, providing attackers with the advantage of surprise. Since the vulnerabilities exploited in zero-day attacks are unknown, there are no pre-existing patches or defenses to prevent them.
A notable case of a Zero-Day attack is the Stuxnet worm, discovered in 2010. It targeted Iran's nuclear facilities, exploiting multiple unknown vulnerabilities in Microsoft Windows and Siemens software. Specifically designed to disrupt Iran's uranium enrichment program, Stuxnet showcased the potential impact of Zero-Day attacks on critical infrastructure, emphasizing the need for strong cybersecurity defenses.
Phishing
Phishing is a type of cyber attack in which attackers employ deceptive emails, messages, or websites to deceive individuals into divulging sensitive information, such as passwords, financial details, or personal data. Phishing emails often include malicious links or attachments. Clicking on these can install malware on the user's device, granting attackers backdoor access, facilitating additional attacks, or compromising the entire network. That's why I mentioned earlier that it's crucial to educate your employees about information hygiene and cybersecurity.

If you are looking for a software development team that will make you a secure website or application, contact us. Our team at Movadex is dedicated to creating bespoke solutions that align seamlessly with your business objectives. To learn more about how our software services can elevate your cybersecurity, feel free to contact us at nor@movadex.com or schedule a complimentary call directly here. We look forward to assisting you on your path to optimized digital solutions tailored to your unique requirements.